
Scaling Operation of Microsoft 365 for Different Protection Requirements
Microsoft 365 and the DELOS cloud are revolutionizing traditional IT workplaces
The public sector is diverse. The focus of public perception is usually only on the state bodies, states, and municipalities. However, the public sector includes not only public authorities, but also police, fire departments, schools, universities, health insurance companies, hospitals, and organizations in the construction and housing sectors.
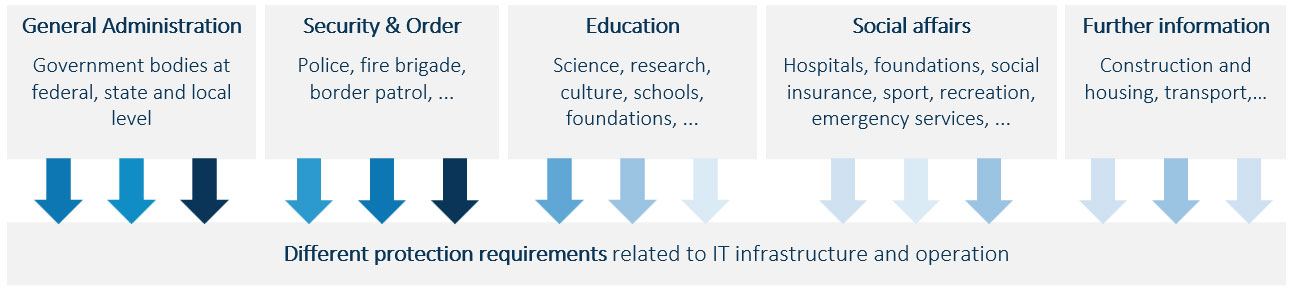
This diversity is why in-house or external IT service providers must meet different requirements, even if most of their customers are in the public sector.
Many public authorities have not yet been allowed to take advantage of the cloud
Many public sector organizations were previously denied access to the cloud. The benefits associated with the development of cloud technology advantages they have hardly been able to take advantage of. Working together in the same document, using different end devices simultaneously, access via links, and regular updates: The IT workplace has only been able to do all of this since it was converted to the cloud model.
But why do so few government organizations currently take advantage of these benefits to date? The reason lies in the high protection requirements of public institutions. While private-sector companies concentrate on complying with data protection regulations and ensuring the security of data centers and software, public authorities need to prepare themselves for the occurrence of unique risks.
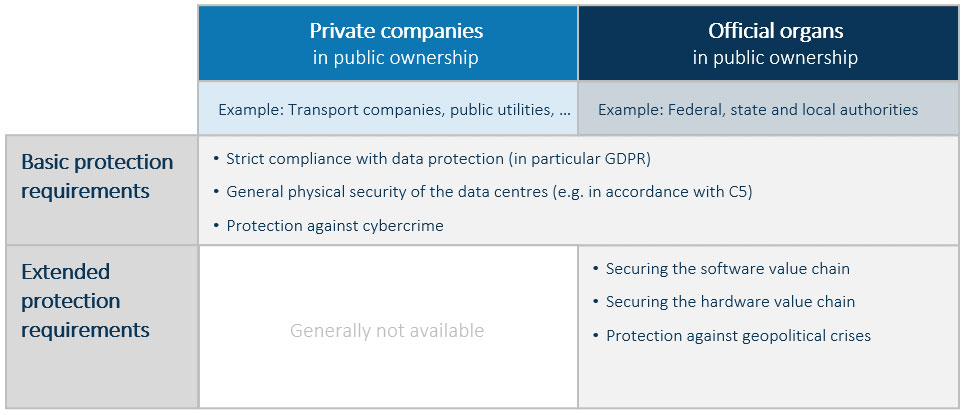
With cloud technology, protection against cyber criminals can now be achieved very well, and, in some cases, even better, with cloud technology. In turn, Microsoft required special efforts in close cooperation with the BSI to achieve more excellent crisis resistance in IT value creation.
The DELOS cloud offers a model that enables German companies to use Microsoft technologies. In addition, the hardware and software supply chains of Microsoft 365 are specially secured based on this model. As a result, the cloud achieves a high degree of digital sovereignty and protection against geopolitical conflicts that are otherwise only known from private clouds.
Microsoft offers clouds for different protection needs
US companies largely drove the development of traditional IT towards integrated cloud offerings. With the establishment of the first cloud data centers in Europe in 2009, companies were also able to start storing their content data locally. To ensure the smooth operation and further development of its own services, Microsoft still had to export a small amount of telemetry and support data from Europe until recently.

In 2023, Microsoft will gradually introduce an "EU data border" introduced. With this option, customers can choose whether telemetry and support data should remain within the EU besides content data. The DELOS cloud will be available for extended protection requirements starting in 2026.
From IT infrastructure and operations to more Users: inside reference
There is now a suitable cloud for every protection requirement. But how can different protection classes be operated centrally across the various clouds?
The answer to this question lies in a cloud migration project. If an organization leaves the traditional data center and moves its workplace IT to the cloud, its own performance changes significantly. Before the migration, the organization's own employees still had to install and operate hardware (such as servers, storage, and networks) and install, operate, and update the various applications (such as mail servers, file storage, and video conferencing systems).
The focus is now on activities that are close to the users users: The secure configuration of their rights, roles, access, and end devices, as well as related operational tasks.
Microsoft CrossTenant-Access as the key to scalable operation
The following Microsoft tools play a crucial role in centralizing and scaling these configuration activities:
Microsoft Entra-ID: With the help of the Active Active Directory (Azure AD), all user accounts, groups, and authorizations are managed. It offers extensive setting options for applications in the cloud and local environments. It also provides a high level of convenience for users, for example, through single sign-on (SSO). It improves security, for instance, through multi-factor authentication (MFA) and fraud detection based on unusual usage behavior.
Microsoft CrossTenant Access: This tool is based on the Entra-ID and simplifies the management of different tenants: tenants) by service providers or IT departments. The key to this is: Administrators no longer have to manage their own users for each customer to be addressed, but can complete their tasks centrally with their user account. This is achieved through intelligent management of access across different clients (cross-tenancy).tenant) across different clients.

So, provided all clients manage their identities with Entra-ID, these can be managed with the help of cross-tenant Access (federated Access). Federated). In this way, central IT teams can take over the administration of very different organizations with differing protection requirements on a scalable basis. Thanks to the extensive security functions and the very fine-grained rights/role options, this is done while maintaining very high compliance standards. In addition, very comprehensive reports on user activities, authentications, and authorizations can be created anytime.
In addition to clouds for different protection requirements, Microsoft 365 offers IT departments and service providers extensive options for optimizing operations without sacrificing IT security and ease of use.
Arvato Systems aims to make the public sector's IT workplaces fit for the future and increase employee productivity. As a professional in digitalization in the public sector, the company knows the needs of the industry and supports you in all technical and organizational challenges.
Written by
